This blog will explain the normal aftercare that needs to happen after an SAP system is upgrade or has been patches with support packages.
Questions that will be answered:
- What is the normal processing sequence in SPAU?
- What is the new SPAU_ENH transaction?
- Which aftercare is needed when using embedded search via TREX or HANA?
- Which aftercare is needed for the authorization team?
- What are the general sanity checks after an upgrade?
- How to regenerate SAP_ALL and SAP_NEW?
- How can I check for new or altered security parameters?
- What other things to do after upgrade?
- SEGW issues after upgrade, how to solve them?
- How do I check for new security parameters?
SPAU processing
For extensive explanation on SPAU, read the dedicated blog. The below is a summary.
When starting transaction SPAU in a netweaver 7.50 or higher system the screen will look as follows:
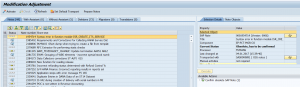
First thing to do is to hit the Reset OSS notes button or Prepare OSS notes button (the name can differ bit per version):
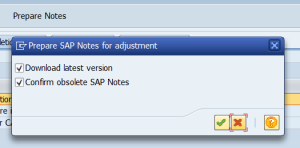
This will download all OSS notes again and automatically mark the obsolete ones and will remove them from the list. Wait until the batch job doing this job for you is finished. This will save you a lot of time.
In a 7.50 or higher system look at OSS note 2532229 that solves a bug with notes in adjustment mode.
Second step is to process all the OSS notes. Don’t start the other activities until the OSS notes are done.
Third step is to process the tab With Assistant. Only when this is done continue with the tab Without Assistant.
The steps Deletions, Migrations and Translations are optional, but best to do as well. Deletions can be many, but here you can select all and reset to SAP quite quickly.
SPAU_ENH to process enhancements
Often forgotten is the post processing with transaction SPAU_ENH.
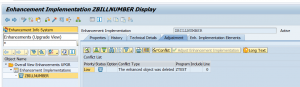
If there are changes in enhancements made by SAP conflicts with customer implementations can occur. SPAU_ENH will list them, and you can process them. If forgotten the customer implementation might not be called, which can lead to functionality giving errors.
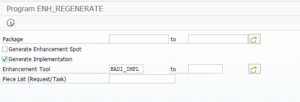
In rare cases you will need to regenerate the enhancement spots via program ENH_REGENERATE. See OSS note 2507482 – ENHO: After System Upgrade, BADI_SORTER for BAdI Implementation is not being triggered:
RTCCTOOL post processing
After any upgrade/support package the basis person must run the RTCCTOOL program. This will check and list any needed updates.
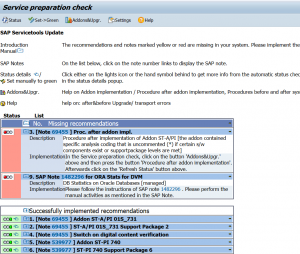
In almost all cases the actions behind the button Addons&Upgr must be triggered by the basis person.
DMIS plug in OSS notes
If you are using the DMIS plugin for SLT, then you need to run the DMIS note analyzer program(s) again after the support package or upgrade. More information: read this blog.
| Scenario | Report name |
| Object Based Transformation (OBT) | CNV_NOTE_ANALYZER_OBT |
| ABAP Integration for SAP Data Intelligence (DI) | CNV_NOTE_ANALYZER_DI |
| S4HANA Migration Cockpit (MC) | CNV_NOTE_ANALYZER_MC_EXT |
| SAP Landscape Transformation (SLT) Replication Server | CNV_NOTE_ANALYZER_SLT |
| Near Zero Downtime Technology (NZDT) | CNV_NOTE_ANALYZER_NZDT |
Embedded search post processing
With an upgrade or support package SAP will deliver new improved version of embedded search models. If you are using embedded search you have to do post processing to make use of these new improved versions.
By default SAP will keep using the old model to make sure the search function keeps working. The basis administrator can then update the search models at their convenience.
To update start transaction ESH_COCKPIT:
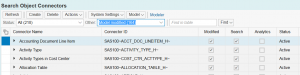
Then from the Other drop down select the option Model modified:
Note: if there are no Model modified present, but you do get the message like "update in background started", then wait until the model update background job is finished. This job can take long time. If finished restart transaction code ESH_COCKPIT again.
Select all to be updated (or in case there is a lot a subsection). Then select from Actions menu the Update option:
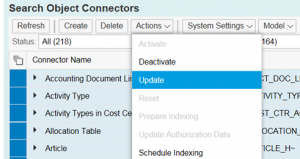
Then you have to wait (a lot). Even on HANA this will take a long time.
You might get a message that you yourself are locking the update process: in this case, wait until your processes in the background are done (SM66 monitoring) and then try again, or use smaller selection.
Alternative is to delete the search model after the upgrade and redo completely. For setting up search model in S4HANA read this dedicated blog.
Background OSS note: 2468752 – Re-indexing after an application Upgrade.
Authorization post processing
With any upgrade or support package SAP will deliver new authorization objects. These need to be handled as well.
Regenerate SAP_ALL and SAP_NEW
SAP_ALL needs to be regenerated. This can be done simply by starting transaction SU21 and hitting the Regenerate SAP_ALL button:
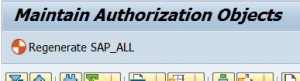
See also SAP note 410424 – Customizing for generation of profile SAP_ALL.
SAP_NEW can be regenerated with program REGENERATE_SAP_NEW:
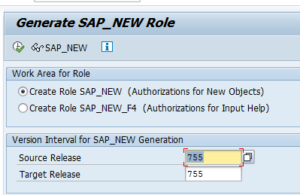
See OSS note 2606478 – REGENERATE_SAP_NEW | bridging authorizations for input helps.
SU25 profile generator post processing
The authorization team needs to do post processing in the SU25 transaction to update profile generator.
Upon starting this transaction after the upgrade or support packages it will prompt you for having checked OSS note 440231 (SU25 preparation FAQ note).
Do download the most recent version (redownload the OSS note!) and read the content. The note cannot be applied automatically (it will say cannot be implemented). This is because it is a FAQ note. If you open the content scroll to your version and check the OSS notes. Make sure the notes listed there are applied to your system before continuing with SU25.
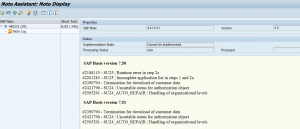
Then startup SU25 again and process steps 2a, 2b and 2c:
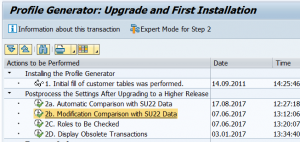
More background information can be found in SAP note 440231 – SU25 | FAQ: Upgrade postprocessing for Profile Generator.
Standard SAP job updates
After any SAP support package or upgrade, SAP will improve and/or change the standard clean up jobs.
To do this: go to SM36 and click the button Standard Jobs. Then select the Default Scheduling job. Then the system will tell you which jobs will be stopped (no longer needed), changed and new jobs there will be planned. See also the technical clean up blog.
For S4HANA standard jobs, read this blog.
Update of IMG nodes
If you use custom IMG nodes, you have to re-integrate your node into the main IMG using transaction S_IMG_EXTENSION. For more information see the blog on setting up custom IMG nodes.
Updating requirements and formulas
After an upgrade or support package the requirements and formulas might need to be regenerated via program RV80HGEN. More details: read this blog.
Updating ABAP where used list
After an upgrade or support package the ABAP where used list must be regenerated again. Read this dedicated blog.
Security parameters
With an S4HANA upgrade, the is a program to run to check for new security parameters: RSPFRECOMMENDED. Read this dedicated blog for details.
General sanity checks after an upgrade
The basic sanity checks after an upgrade actually start before the upgrade!
Before the system is being upgraded, you should check following items:
- ST22 short dumps
- SM37 batch job failures
- SM13 update failures
- SM58 RFC failures (for idocs and qRFC)
- SM21 system log issues
If you check this at regular intervals before the upgrade you get a good mental picture (you can also take screen shots before the upgrade) of the issues already present in the system.
After the system upgrade and/or support package you check these items again. Because you checked before it is easy for you to see and filter out new items. New items can be analyzed for solution (can be SAP note that is needed, custom code that is not properly updated, changes in functionality, etc).
SGEN code generation
After support pack or upgrade you can use transaction SGEN to generate all ABAP code (standard SAP and custom) and check for errors in code generation. More information in this blog.
SEGW issues on standard SAP after the upgrade
In the past you could solve SEGW FIORI ODATA exposing issues directly in the system. Now SAP has forbidden this. See OSS notes 2734074 – Editing of standard SEGW projects for customers is blocked and 2947430 – Editing Standard OData Service Project throws error: Editing Prohibited SAP delivered projects cannot be edited in your system. The emergency workaround is described in OSS note 3022546 – In Transaction SEGW, Error ‘SAP delivered projects cannot be edited in your system’ is encountered during change of the OData Project PS_PROJFIN_MNTR.
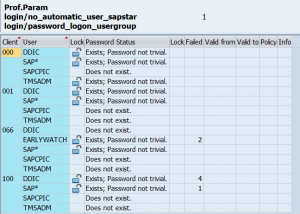
Check for new or altered security parameters
After a support pack most security parameters remain the same. After and upgrade you need to check for new or altered security parameters. For S4HANA upgrade there is special note and program to quickly check for new and altered security parameters including the SAP recommendation: read more in this blog.
Other things to do after an upgrade
After an upgrade you can scan and check for new or enhanced functions you can use.
Examples to check:
- Update the SCI variants delivered by SAP (see blog)
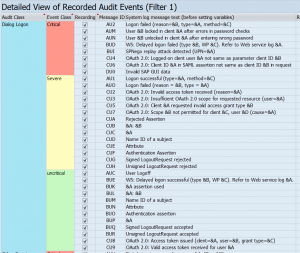
- SAP audit logging will deliver new checks, but these are deselected after the upgrade
- If using enterprise search: check if SAP delivered new search models that might be interesting for the business