RFC security is a cumbersome job. There are programs to help speed up the security checks for RFC connections.
Questions that will be answered in this blog:
- How to quickly check all the RFC’s in my system?
- How to quickly check the trusted RFC’s in my system?
Hacking using RFC connections
RFC callback hacking: read this blog.
RFC jump hacking: read this blog.
Check RFC connections
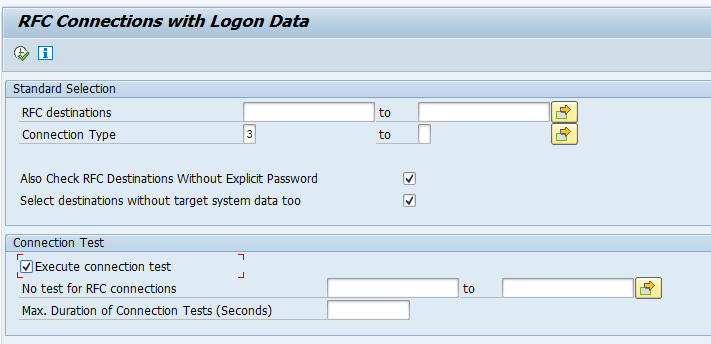
Program RSRFCCHK (which also has the same transaction code RSRFCCHK) can quickly scan all your RFC’s. In the selection screen, please make sure to select the 2 extra boxes for “Also check RFC destinations without explicit password” and the “Select destinations without target system too”:
The connection test is optional. But if the RFC is not working, then you might consider it old and no longer needed. In this case you can perform the clean up by deleting the RFC.
The output of the report RSRFCCHK, you can use to look for:
- RFC’s with personal user ID
- Cross system layer RFC’s (from production to development, or from development to production)
- Trusted connections where you don’t expect them
- Old destinations no longer in use
As a best practice at least yearly check on every system the RFC's that are setup there. Read this blog on how easy it is to use wrongly configured RFC's to hack a system.
OSS notes:
- 3283474 – Adjustment of authorization for program RSRFCCHK.
- 3453471 – RSRFCCHK: Wrong message: TMSADM has too many authorizations
- 3486623 – RSRFCCHK outputs incorrect value for T/T
- 3497859 – How to use report RSRFCCHK?
Check trusted connections
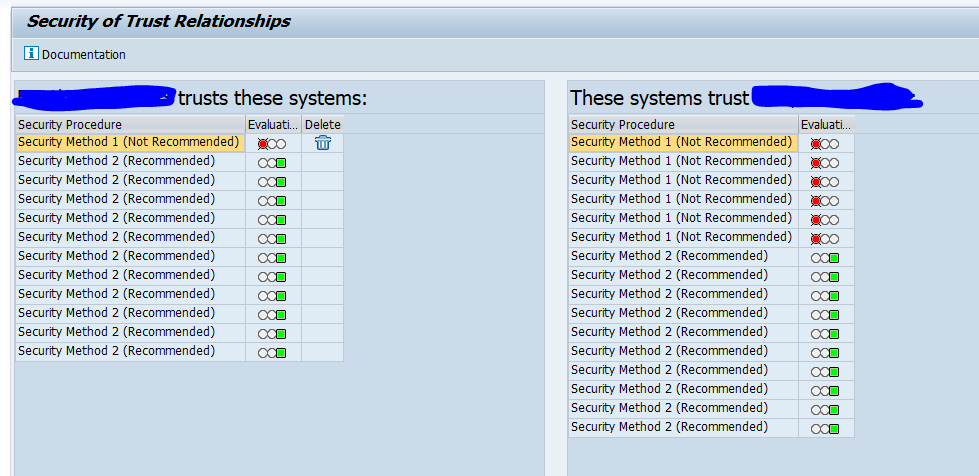
To check trusted connections run program RS_SECURITY_TRUST_RELATIONS. Output example:
The red lights should be investigated and fixed.
More on setting up trusted RFC’s is written in this blog.
SAP standard on RFC security
OSS note 2008727 – Securing Remote Function Calls (RFC) contains a very extensive PDF explaining all ins and outs on RFC security.