In SAP there is a user exit just behind the logon of a user. This can be used correctly, but also used for hacking.
Questions that will be answered in this blog are:
- How to switch on the user exit after logon?
- What is good use of the user exit after logon?
- How to use the user exit for hacking?
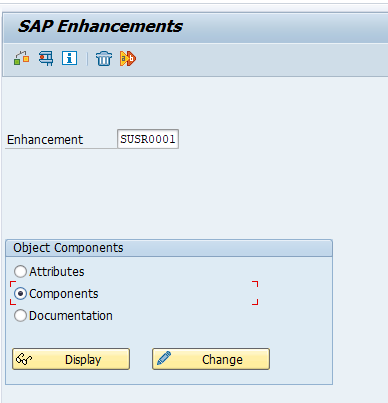
Activation of the user exit
In transaction SMOD you can call up user exit SUSR0001:
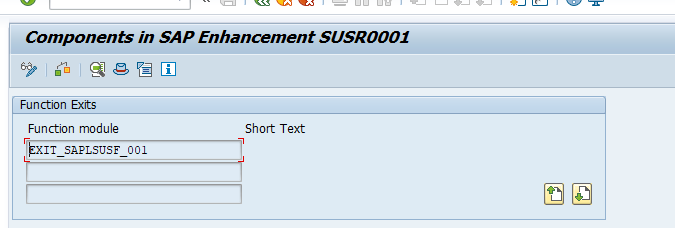
This exit has only one component:
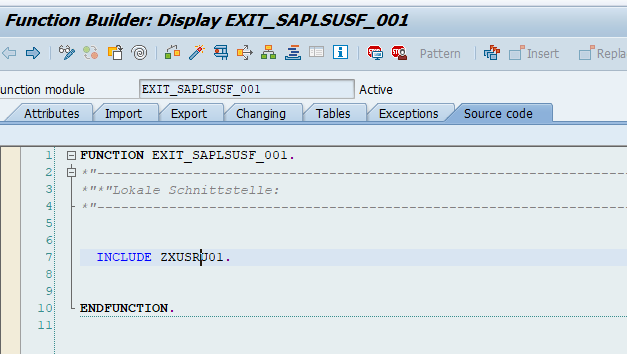
Double click on the exit to go to the Z code include:
To activate the exit, create a project in CMOD and and include this enhancement. Then double click on the include code ZXUSRU01 to activate the code.
Good use of the user exit
The user exit itself is described in OSS note 37724 – Customer exits in SAP logon. Example of good use it to restrict multiple logons in case you cannot switch on parameter login/disable_multi_gui_login. See OSS note 142724 – Prevention of multiple SAPGUI logons.
The exit is also used a lot by GRC and firefighter type of tools.
For ITS webgui the calling of the logon user-exit can be skipped with a URL parameter. See OSS note 1465767 – Logon user exit SUSR0001 not called.
The user exit logon hack
In the user exit code, you can put in your own stuff.
As hacking example: copy function module PASSWORDCHECK and the screen that belongs to it to your own ZPASSWORDCHECK.
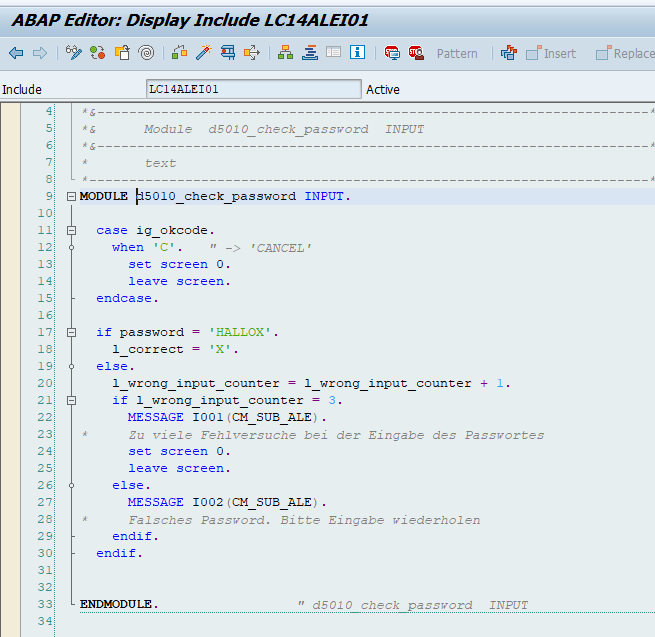
Modify the screen logic a bit. This is the original code:
Now change the code: the password is always reported back as ok. And the user input you catch in the field password is yours: you can mail it or store it somewhere for you to pick up later.
Put the altered code in the user-exit with logic:
IF SY-UNAME = 'target user name' and not capture before. CALL Z function ZPASSWORDCHECK. Store capturing. Set capture flag. ENDIF.
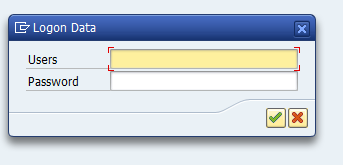
This looks as follows at runtime:
Many end users (and even auditors) will enter their password without thinking twice.
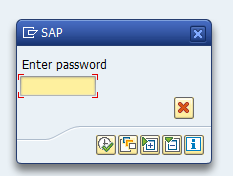
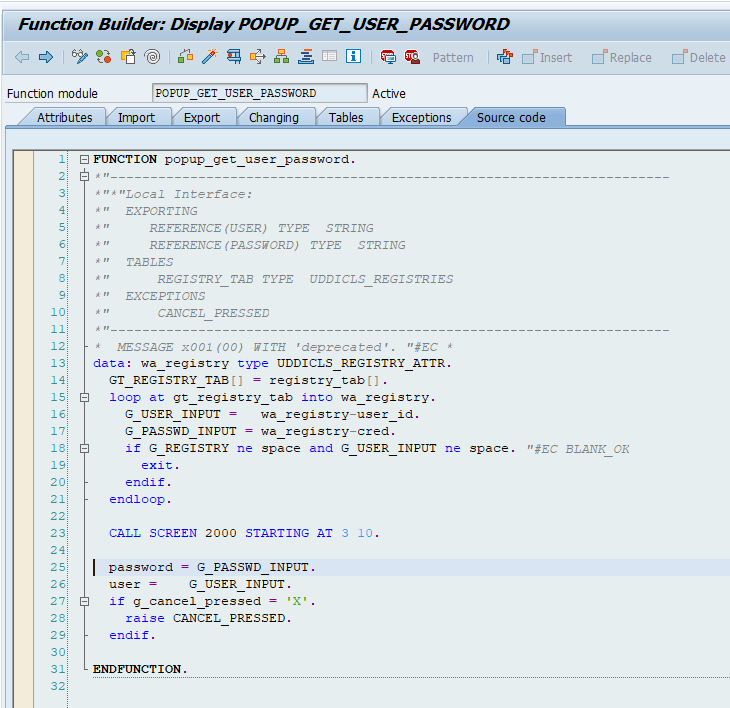
Alternatively you can use function module POPUP_GET_USER_PASSWORD as a basis for your copy: this has also clear text password:
The password field can be stored.
This has the following look and feel:
Detection and protection
It is wise to shield off this user exit from improper use and to yearly check the content of what is inside this user exit.