This blog will explain the SAP audit log.
Questions that will be answered are:
- What is the intended goal of the SAP audit log?
- How to switch on the SAP audit log?
- What are the recommended settings for the SAP audit log?
- What are the common issues with audit logging?
- Can I get anonymous access to the audit logging?
- How can I get statistics on audit logging?
- How can I get a where used list from the audit logging?
- How can I archive audit log data for long term storage?
- How can I delete audit logging?
Goal of SAP audit log
The goal of the SAP audit log is to capture all audit and security relevant actions. The audit logging function can capture failed logon attempts, dangerous actions like debug & replace, execution of transactions and programs, and many more.
SAP has a note for the frequently asked questions: 539404 – FAQ: Answers to questions about the Security Audit Log.
Also interesting read is this note: 3352573 – How to check transactions executed by an user in AS ABAP.
Audit log and privacy
The audit log will capture actions performed in the system. It will not only capture the actions, but also the user ID and terminal ID. This makes the tool a bit of a big brother is watching you tool. Auditors are normally used to dealing with sensitive topics. But next to answering audit questions the audit can also be misused to check ‘is this person doing a lot of work in the system’. For this reason access to audit log should only be given to persons who understand the sensitivity and people privacy. This includes in giving information to managers extracted from the audit log.
Anonymous audit log reporting
In the SAP audit log user names and terminal ID’s are visible. This is in many cases privacy information. Due to privacy rules and regulations the audit log access might be very restricted or cumbersome. Especially when the audit logging is to be used for analysis purposes, rather than for audit. If OSS note 2883981 – RSAU_READ* | anonymized display of Security Audit Log data is applied, a new transaction is created. This new transaction, RSAU_READ_LOG_ADM, shows all the information, but now with user ID and terminal ID columns in anonymous mode.
Switching on the audit log
For switching on the audit log first the corresponding system parameters must be set:
- rsau/enable: set to 1 to enable
- rsau/local/file: set the file location in format “/usr/sap/<SID>/<instno>/log/
audit_<SAP_instance_number>” (yes, unfortunately audit log still uses a file) - rsau/max_diskspace_local: max disk space (set to at least 1 GB)
- rsau/selection_slots: default is 2, but typically this is set to 10 slots
Unfortunately these parameters are not dynamic, which means a system restart is required to activate these parameters.
After the activation you can go to transaction SM19 (or in newer version to RSAU_CONFIG) to switch on the audit logging in detail.
First step is to create a profile and activate it.
Next step is to setup the filters.
Audit log filters
The audit log filters are used to filter events. If you select all events this will cause logging shadow and make the function unreliable.
To configure the filters use transaction RSAU_CONFIG (this is replacing old SM19 transaction).
Main client versus 000, 001 and 066 client
SAP has multiple clients. The 000, 001 and 066 client are only used by system admins. For these clients you can setup a special filter and log ALL actions for ALL users. This will not cause too many entries.
If you want to fully avoid SAPSYS entries, follow the instructions from this blog section.
Main client logging settings
In the main client you have to be selective on the checks.
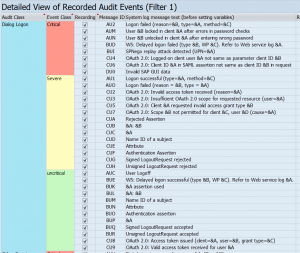
The audit log has 3 classification of checks:
- Critical (always switch these on!)
- Severe (if possible switch on as well)
- Uncritical (be very selective for switching these on)
Key filters recommendations
ALWAYS switch on the critical checks. This will include:
- Debug & replace actions
- Debug start
- Changes to audit log configuration itself
- User creation
- Failed logon attempts
- User locks due to wrong password
From the severe and uncritical sections the following checks are useful:
- Logon failed: this can help to detect logon attempts with standard users (see blog on SAP standard users): the audit log will capture the terminal ID from which the attempt happened
- Start of report failed: will avoid discussions if people really could start or not
- Report started: though in many productive systems SE38 etc is not allowed for directly starting a report outside a transaction code, this still will happen by admins and firefighter. This check will log which direct report is started
- Transaction locked and unlocked: capture locking and unlocking of transactions with SM01 in old systems (and SM01_DEV and SM01_CUS in newer systems)
- Transaction started: this will avoid discussion if people key in the tcode or not (do remember that audit log captures the start; it can still be user is not authorized to continue with the transaction). And many RBE (reverse business engineering) type of tools rely on this audit log tracing rather than the ST03 logging. Reason is that the audit log is on user level rather then aggregated level and is usually kept longer.
- User deleted, user locked and user unlocked
- Password changed for user
SE92 audit log details
Using transaction SE92 you can get a more easy overview of the settings definitions as provided by SAP for the audit log details. Read more in this blog.
RSAU_CONFIG configuration overview
Using transaction RSAU_CONFIG you can get a more easy overview of the actual activation and configuration.
Audit log reporting
Transaction codes SM20 or RSAU_READ_LOG can be used to view the audit log results.
Be careful to whom you give the rights to read the audit log.
Audit log settings overview
You can use transaction RSAU_CONFIG_SHOW to get an overview of the audit log settings.
New checks
With every new SAP release SAP improves the audit log. By default the audit logging is not updated after an upgrade. Therefore it is wise to check for new items added to the audit log after an upgrade.
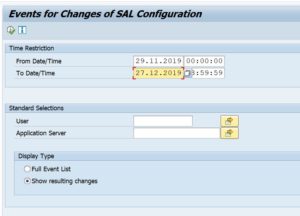
Determining changes to audit log settings
OSS note 2680888 – SAL | Report for determination of differences in event parameters is delivering new report RSAU_READ_LOG_DIFF to show changes done to the audit log configuration:
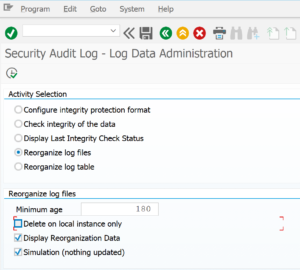
Delete SAP audit log files
Start transaction RSAU_ADMIN and start the option for log file reorganization:
Or you can run/schedule program RSAUPURG.
Restricted access to this function is a must.
Archiving audit logging
There might be requirements from security or business side that require you to find a solution for long term storage of the audit log data. Deletion as explained above could not be an option for you.
To archive audit logging data, activate the settings for archiving object BC_SAL. Read this blog on the exact technical execution of archiving runs.
OSS notes to be applied for the audit log archiving function:
- 3014220 – RSAU_ARCHIVE_READ | Optimization of evaluation
- 3054172 – Audit log archive management
- 3063886 – RSAU_ARCHIVE_DELETE | SARA Statistics
- 3068475 – RSAU_ARCHIVE_WRITE | Optimization and functional enhancements
- 3081540 – RSAU_ARCHIVE_WRITE | UNCAUGHT_EXCEPTION CX_PARAMETER_INVALID_RANGE
- 3094328 – RSAU_ARCHIVE_RELOAD | Reloading Security Audit Log archives
- 3232857 – RSAU_ARCHIVE_WRITE | Archive up to current date not possible
- 3281751 – BC_SAL | Masked error message for archiving of audit log data
- 3323638 – Performance optimization for RSAU_ARCHIVE_DELETE
Issues with audit logging
There are some known issues with the audit logging.
Logging shadow
If too much items are selected in the filters the audit logging will grow very fast. If the audit log is full, it will start to overwrite the earlier entries. The earlier entries are then lost. This is called logging shadow. Depending on your requirements, you have to increase the disk space, and better: check which item in the audit log settings you don’t need, but do cause extensive amount of logging.
Large SAP systems with multiple application servers
On large SAP systems with multiple application servers, the file handling can cause issues. If the system is setup using shared files and the names of the profile configuration per application server for the file name is identical, this will cause nasty issue. The issue is that the audit logging from several application servers will overwrite each other entries. This is hard to detect. Solutions: don’t use shared file, or change the profile parameter per application server to include the application server name into the audit log file name. To do this set the FN_AUDIT parameter to this value: SQL_++++++++.AUD. Upon runtime the +’s will be replaced with the application server name.
Be sure to read OSS note 2367475 – “Profile parameter FN_AUDIT contains an invalid pattern” in system log in this case as well.
See also point 25 in the audit log FAQ note 539404 – FAQ: Answers to questions about the Security Audit Log.
Audit logging integrity
Based on the settings in OSS note 2033317 – Integrity protection format for Security Audit Log, you can switch on the audit logging integrity. This way you can prove nobody tampered with the audit log. But this also means you cannot read the audit logfile on file level or by any third party tool. Please consider this carefully and read the note about other effects and prerequisites first before switching on.
Where used list and audit log statistics
On newer versions (or via notes below) there are 2 new programs available:
- RSAU_GET_STAT for statistical information
- RSAU_GET_WUSL for a where used list of security events
To get this function apply these OSS notes:
Audit log self check
To get this function apply the same notes as for the audit log statistics:
- 3002091 – RSAU_READ_LOG | optimization of message statistics
- 3145365 – RSAU_SELF_CHECK_DIA | Enhancement of environment check
Then you can run program RSAU_SELF_CHECK_DIA.
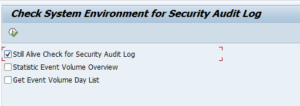
If you want to run the Still Alive Check:
You first have to make sure to activate Audit test event AU0:
Background OSS notes and blogs
Logging incidents for SAL (SAP Audit Log): 3295213 – Required information for analyzing issues with the Security Audit Log (AS ABAP) within the new SAL environment.
Useful background OSS notes and blogs are:
- Audit log FAQ note 539404 – FAQ: Answers to questions about the Security Audit Log.
- 1941568 – SAL | FAQ for use of customer-specific events
2191612 – FAQ | Use of Security Audit Log as of SAP NetWeaver 7.50
- 2360334 – Security Audit Log does not work after setup
- 2414468 – Analysis of SAL log data in the background
2546993 – Analysis and Recommended Settings of the Security Audit Log (SM19 / SM20)
- Blog on recommended security audit log settings
2676384 – Best practice configuration of the Security Audit Log
- 2995772 – How to Specify Massive Audit Files to be Searched with RSAU_READ_LOG and RSAU_SELECT_EVENTS
- 3055825 – RSAU_LOAD_FILES for transferring audit log data to the SAL database
- 3090362 – RSAU_ADMIN | Integrity protection format – data management
3094328 – RSAU_ARCHIVE_RELOAD | Reloading Security Audit Log archives
- 3097820 – Configuration of “Maximum Size of One Audit File” is incorrect – Audit log in ABAP system
- 3113752 – User logoff entry not captured in audit logs.
- 3237752 – Security Audit Logs not recorded when using NFS storage
- 3137004 – How to archive audit log from DB?
- 3140539 – SAL | New event definition for change access in SE16N
- 3143980 – How to activate a static profile in T-Code RSAU_CONFIG
- 3144105 – How to apply the configuration of a static audit log profile to the dynamic configuration without system restart in RSAU_CONFIG
- 3218604 – Troubleshooting user logon problems
- 3219561 – Where to find information about the Security Audit Log and it’s configuration ?
- 3225726 – Logging the Client IP address in the Security Audit Log when using SAP Web Dispatcher.
- 3226223 – How to monitor debug activities in SAP Netweaver.
- 3233604 – How to check RFC logon lock or failure issue in security audit log
- 3265014 – New events FUG, FUH, and FUI
- 3274589 – New events FUJ and FUK
- 3298279 – New event FUL (shared object topic)
- 3319853 – SAL events for DBA Cockpit
- 3386875 – SAL Event FUR for File Share Client
Known bugs and bug fixing OSS notes
Bug fixing OSS notes:
- 2841034 – Security Audit Log: AU3 entry for core transaction of variant transaction
- 2902365 – Enhancement of RSAU_COLLECT_STAT_DATA
- 2903947 – Unnecessary event logging
- 2919024 – RSAU_READ_LOG | Reading of logs for inappropriate parameterization
- 2936390 – RSAU_SELECT_EVENTS displays incorrect instance for local search
- 2990798 – Original virus scan profile is not listed in Security Audit Log
- 2993146 – SM20/RSAU_READ_LOG | problem when reading from files
- 2998269 – RSAU_READ_LOG | error when displaying the interval of data actually read
3038925 – RSAU_SELECT_EVENTS | Statistics information in the list header
3053695 – RSAU_ADMIN | Reorganization of log files after change of FN_AUDIT
3068475 – RSAU_ARCHIVE_WRITE | Optimization and functional enhancements
3080892 – SAL | Conversion error when saving numeric parameters
3081540 – RSAU_ARCHIVE_WRITE | UNCAUGHT_EXCEPTION CX_PARAMETER_INVALID_RANGE
3086916 – SM20/RSAU_SELECT_EVENTS | unsuitable short texts for security level
3089438 – Missing transaction start (AU3) entries in the Security Audit Log
3090362 – RSAU_ADMIN | Integrity protection format – data management
3090494 – RSAU_READ_LOG / SM20 | Transaktionskontext für Audits
3097820 – Configuration of “Maximum Size of One Audit File” is incorrect – Audit log in ABAP system
3102375 – Inconsistent entries in Security Audit Log for events of type AU5 and AUK
- 3150788 – Security Audit Log information on the used transaction-code is unavailable.
- 3205227 – Transaction execution log missing in the audit log
- 3249114 – Optimization of APIs for reading the audit log
- 3261220 – RSAU_ADMIN | Options on the selection of T-Code RSAU_ADMIN are greyed out
- 3298908 – RSAU_MAINT_LOG | job with error message ‘Trigger () does not exist in table RSAU_SYNC’
- 3308752 – API RSAU_API_GET_ALERTS does not find any data
- 3346306 – RSAU_ADMIN | Allow Reorganization of data for recording target database – API mode
4 thoughts on “SAP audit log”