This blog series will explain the process of hacking SAP password hashes: also know as SAP password hacking. The process of hacking will be explained and appropriate countermeasures will be explained.
Questions that will be answered are:
- Where are SAP password hashes stored?
- Which software do I need to install for hacking the password hash?
- How does the brute force method work?
- How does the simple 10k most used password list attack work?
For follow up blog on hacking SAP PASSCODE, click here.
For follow up blog on hacking SAP PWDSALTEDHASH, click here.
For follow up blogs:
- Improving attack speed by applying rule-based attack, click here.
- blog on optimizing the attack.
- blog on extended word lists
SAP password hashes
SAP has 3 main password hashes:
- SAP BCODE (oldest one and very weak): not to be used any more
- SAP PASSCODE (less old, stronger than BCODE, but still weak): not to be used any more
- SAP PWDSALTEDHASH (newest, strongest)
New SAP installations only use the newest method by default. Older system still might have stored older versions.
From user password to hash
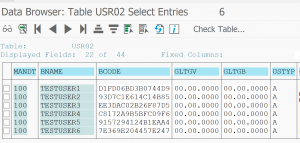
When a users password is set initially or is changed is it hashed and stored in 2 tables:
- USR02, which contains the current password
- USRPWDHISTORY, which contains the history of the passwords
Older systems or wrongly configured systems store all the 3 password types mentioned above.
To start the password attack you need to get the user ID’s and hashes from the USR02 table.
Methods for getting this data (and many more):
- SE11/SE16N table display
- Write simple ABAP program
- Database access on low level (HANA, Oracle, etc)
- …. more creative methods….
For this weeks example we will use a couple of test users. The first 5 users are given simple passwords. The 6th user is given a fully random password.
The attack: from hash back to password
When you have the hashes all of the rest is now outside of the SAP system.
First step is to download a password cracking tool. A very good one is Hashcat.
Warning: this software might be considered as real hacking tool comparable to possessing burglary tools. Either only use on private laptop or after agreement of your local company security team.
Hashcat is based on GPU power and not CPU power. This means the speed of cracking depends on the quality and speed of your graphical card(s). Modern graphics card can have up to 4000 cores. Hashcat is written intelligently to use these 4000 cores via parallel processing or multiple cards.
Download the software from the site and unzip it on your local PC.
Hashcat requires for cracking BCODES the following format per line:
<<USERID>>$<<BCODE HASH>>
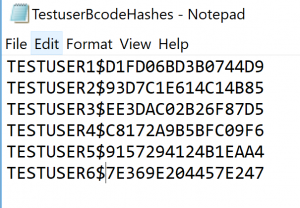
For the example above this results into the following file:
The brute force method
Let’s start by making a file with only TESTUSER6. This is stored in the file TestuserBcodeHashes.txt.
To start the hacking process go to the CMD command prompt, and proceed to the hashcat directory. Then key in this command:
hashcat64 -a 3 -m 7700 -p : --session=all -o "C:\HC\TestuserBcodeHashes_found.txt" --outfile-format=3 --markov-disable --remove --gpu-temp-abort=80 "C:\HC\TestuserBcodeHashes.txt"
Long command, but some part are simpler: -a 3 means brute force, -m 7700 means hashes are SAP BCODE hashes, file output and output, and very important the command to abort if the GPU temperature exceeds 80 degrees Celsius.
For full help options: go to the Hashcat website or key in Hashcat64 –help.
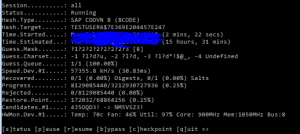
Result of this command is following screen:
The brute force attack will use some common pattern, but as you can see per pattern it takes about 16 hours (faster GPU means less time).
Guessing speed is at 57.000 tries per second, which is about 5 billion tries per day. Having a password with 8 random characters (26 letters, 10 digits, 33 specials) would take 69*69*69*69*69*69*69*69 = 513.000 billion options, meaning it would take 100.000 days.
Pretty good you would say. But nobody uses the brute force method.
Attacking with 10.000 most commonly used password list
People tend to user more simpler and more repetitive passwords. See wikipedia for most common and 10.000 most common used passwords. For full list read this blog.
You can download the file 10.000 most common here: 10k most common
Again we start now Hashcat tool, but now with different command and we will use the file with all the 6 hashes:
-a 6 -m 7700 -p : --session=all -o "C:\HC\TestuserBcodeHashes_found.txt" --outfile-format=3 --markov-disable --remove --gpu-temp-abort=80 "C:\HC\TestuserBcodeHashes.txt" "C:\HC\10k most common.txt"
Attack mode (wordlist) is chosen and we have given the 10k most common text file as wordlist input.
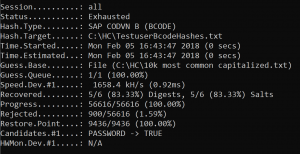
Result:
Recovered passwords: 5 out of 6 in about 0 seconds!
TESTUSER1$D1FD06BD3B0744D9:PASSWORD
TESTUSER2$93D7C1E614C14B85:LETMEIN
TESTUSER3$EE3DAC02B26F87D5:WELCOME
TESTUSER4$C8172A9B5BFC09F6:ILOVEYOU
TESTUSER5$9157294124B1EAA4:STARWARS
You now can logon with these passwords.
This means that we can decrypt the password way much faster than the theoretical example from previous chapter.
How to protect yourself from password hash attacks?
Prevention 1: set password complexity
Set the password complexity rules to at least 1:
login/min_password_digits
login/min_password_letters
login/min_password_lowercase
login/min_password_uppercase
login/min_password_specials
If you have only letters, then the guesses for most users will be 26*26*26*26*26*26*26*26 = 208 billion only. By filtering out the hardly used q and x, it could even be 110 billion only.
Prevention 2: disallow the old hashes
Set parameter login/password_compliance_to_current_policy to 1 to forbid the old passwords to be used (in old systems this might require some testing before it is done in productive system, and changes of old passwords that are there for very long time).
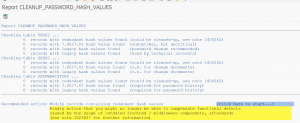
Prevention 3: clean up the old hashes
Use program CLEANUP_PASSWORD_HASH_VALUES to clean up the old hashes (see OSS note 2845609 – How to find user name with legacy hash values when executing report CLEANUP_PASSWORD_HASH_VALUES for detailed manual):
After checking, start the actual cleanup.
More information on program CLEANUP_PASSWORD_HASH_VALUE can be found in OSS note 2845609 – How to find user name with legacy hash values when executing report CLEANUP_PASSWORD_HASH_VALUES.
Prevention 4: instructions to basis and authorization team to use the password generator for initial passwords
When generating new password: do use the password generator button. This will generate very complex password. Do use it.
Also you should make it known to basis and authorization team not to use simple and repetitive passwords like Welcome-2018 or Passw0rd! Soon you will see a pattern and can already guess new users passwords that they will select. Tell them to use the password generator.
Prevention 5: increase hash strength
You can increase the hash strength. This will make the attack last longer, since it simply takes more computing time to try stronger hashes. Read more in this blog.
Next blog
The next blog will explain on the hacking the SAP PASSCODE.

Excellent post. We actually deployed vulnerability monitoring and intrusion detection at clients of all sizes across various industries. Once we even caught a brute force attempt being prepared. An ABAP snippet was caught which would feed data to another password hacking tool, John the Ripper.
Clearly the root cause for this exploit to be possible is the existence of weak password hashes. Correct, it should not happen though it just happens.
Potential attack patterns, which are not only used for hash value extraction, can also be caught red handed.
John the ripper is indeed as well potential tool. It is CPU based. GPU based hashcat is (pending on the money you spend on graphic cards) much and much faster. 10 to 100 times faster even….