Table logging captures all table changes. This blog will answer the following questions:
- How to activate table logging in general?
- How to check if for specific table the logging is active?
- How to check table changes for a specific customizing action?
- How to check general table change?
- How to delete table logging?
- When not to use table logging?
- How can I review table logging for audit purposes?
Table logging activation
In RZ11 system parameter Rec/Client determines the table logging for the complete system. Make sure the value is set to ALL.
See also OSS note 2437986 – SCU3 | How to enable logging in the system. And explanation note 3000730 – Impact on enabling table logging with profile parameter rec/client.
As of new S4HANA 2021 installations or upgrades the activation is done by default: 3093760 – Table Data Change Logs In ABAP Platform.
Table logging per table
In transaction SE11 enter the table you want to check and then go to the technical settings. As example table T000:
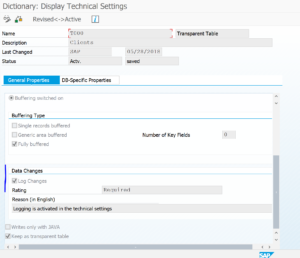
At the section Data Changes you can see that Log Changes has been activated.
Mandatory table logging
In OSS note 112388 – Tables with obligatory logging the mandatory table logging is explained. Which tables are logged is explained in OSS note 2543478 – SCU3 | Which tables are logged?.
If table logging is working properly is explained in OSS note 2523607 – SCU3 | How to check if logging is on.
How to view table changes?
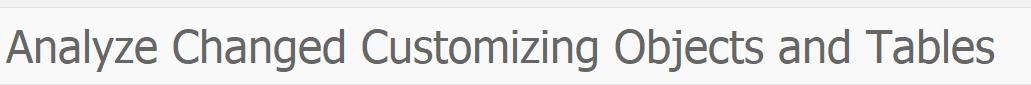
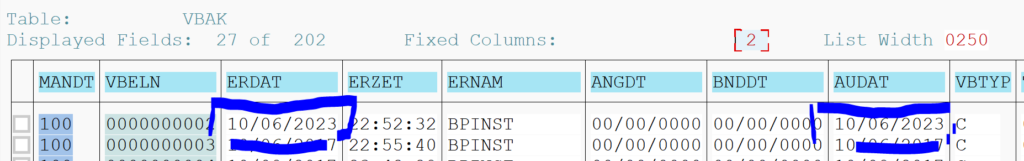
The common way to view table changes is via transaction SCU3. At the start screen press the button analyze logs:
In the next selection screen enter the table to analyze. In this example we analyze table T000:
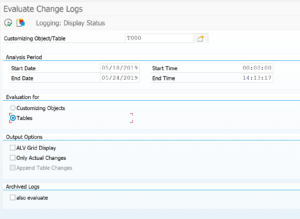
Make sure to set the radio button to Tables. Output of the changes to table T000 then looks as follows:
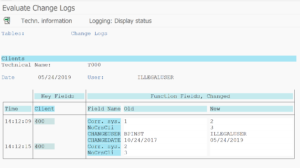
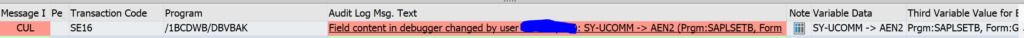
Here you can see changes done by user ILLEGALUSER. At which date and time they were done, and the old and new value.
See also OSS note: 3311577 – SCU3 | How to find out, if table change logs exists for a specific time interval.
Bug fixes:
- 3212410 – SCU3 ALV Change Log does not display the values for INT1/2 fields correctly
- 3400152 – SCU3: Text Table entries repeat for subsequent logs in ALV Grid Display
Checking table changes from customizing
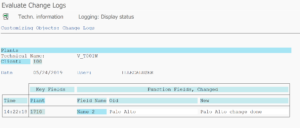
If you are in a customizing action and you want to see who did perform changes, select the menu Utilities and then option Change Log. Select date and time frame to analyze and press Execute. As example here changes to Plant Definition (table T001W):
See also OSS note 3195801 – SPRO | SM30 | How to check the result of a customizing transport and 1834956 – SCU3 | How to enable logging for importing to the system via tp (or R3trans).
Custom tables and standard SAP tables
By default a lot of SAP configuration and important setting tables have the log changes activated. But not all. It is not uncommon to activate table logging for standard SAP configuration tables important for your business. For important custom configuration Z tables you might want to activate table logging.
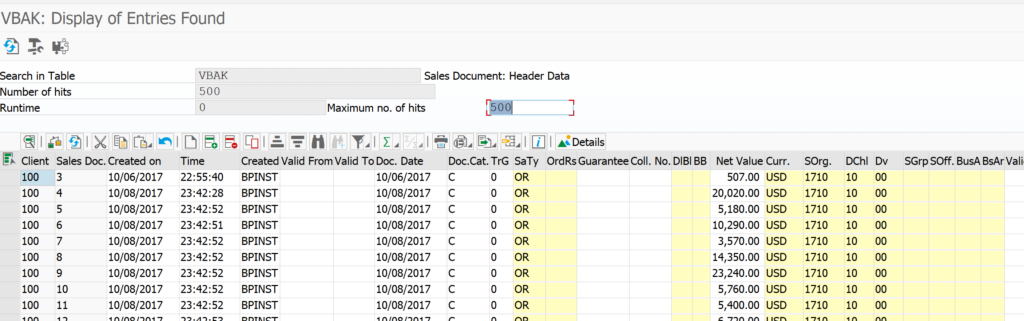
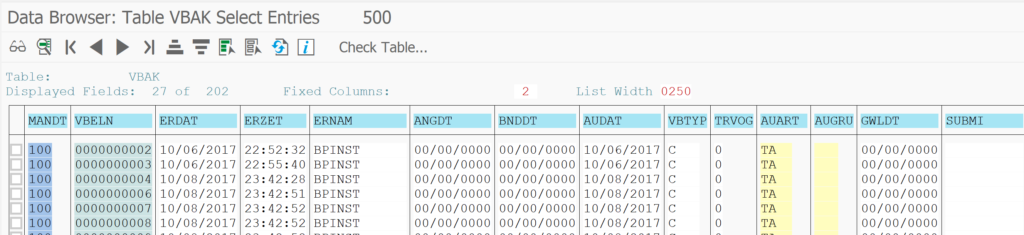
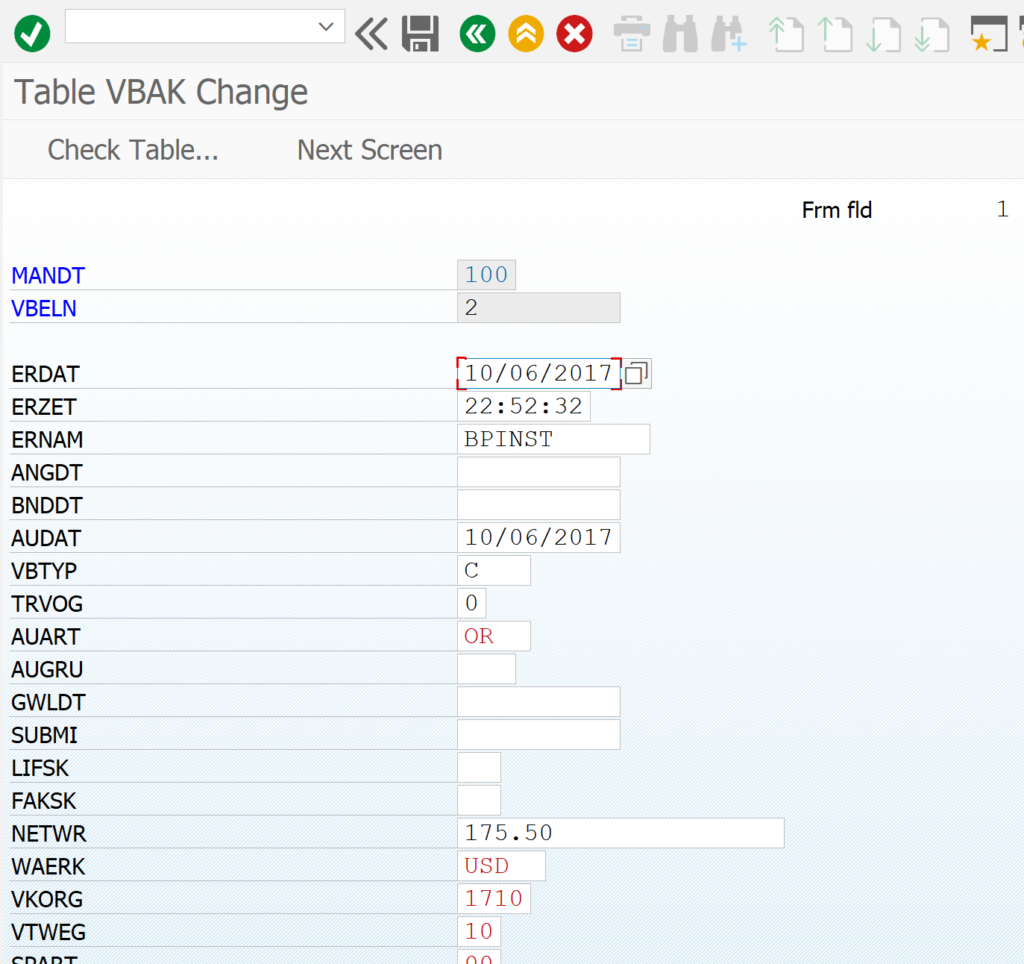
Table logging is not a replacement for change documents. Standard SAP generates change documents for changes to documents that must be kept for tracking and audit purposes. This is common for all major transnational objects and its underlying tables. That is why for example for an important table like VBAK (sales order header) the table logging is off: change documents are already generated.
It is very bad practice to make use of table logging for business data reasons. Table logging is used for recording changes to configuration and if all theses logs are deleted there should be no business impact.
Background OSS note: 3153906 – SCU3 | How to enable logging for tables in customer name space.
Deletion of table logging
Table logging can be deleted with transaction SLG2.
Make sure only very limited amount of people have access to SLG2 and the below program SBAL_DELETE.
SLG2 can run for a long time. For background read OSS note 2507213 – SBAL_DELETE runs too long.
Please be aware the deletion is cross client! See OSS note 3000914 – SCU3 | RSTBPDEL | Caution: The table is cross-client.
Other bug fix notes:
- 2335086 – DBTABLOG | How to detect tables with the highest number of logs
- 2535552 – SCU3: New authorization design for table logging
- 2770800 – Application log deletion table is taking very long time
- 2957039 – DBSQL_TOO_MANY_OPEN_CURSOR in SBAL_DELETE
- 2978235 – Error when displaying table change logs
Review of table logging for audit
OSS note 112388 – SAP system audit | Tables requiring logging explains the audit relevance of table logging and explanation about program RDDPRCHK.
Table logging can be reviewed with program RDDPRCHK:
Bug fixes for RDDPRCHK: